Expiring certificates occur every so often. It is best to have the replaced or renewed before the expiration date.
In our NSX-T environment, the LocalManager, mp-cluster and tomcat certificates are bound to expire. Among others, this will disallow the SDDC Manager precheck on certain clusters to proceed an upgrade.
The LocalManager is used to interconnect with the NSX-T Federation Global Manager.
The mp-cluster certificate is used for external communication with the NSX Manager cluster using the cluster VIP, through UI/API, while the tomcat certificates are used for external communication with individual NSX Manager nodes through UI/API.
This blog post discusses how to replace the self-signed certificates for the above certificates. We will use the LocalManager certificate as an example.
The steps involved are:
- Start a backup
- Request CSR for each self signed certificate
- Create Certificate through the UI
- Activate the certificate using the NSX-T API
- Renewing NSX-T Manager certificates
Start an NSX-T backup
The backup can be created through the NSX-T GUI (System > Lifecycle Management > Backup & Restore)
Request CSR for each self signed certificate
The Certificate Signing Request (CSR) can be created through the NSX-T GUI as well (System > Settings > Certificates)
The details for the CSR can be extracted from your expiring certificate. Open the pull-down box for this.
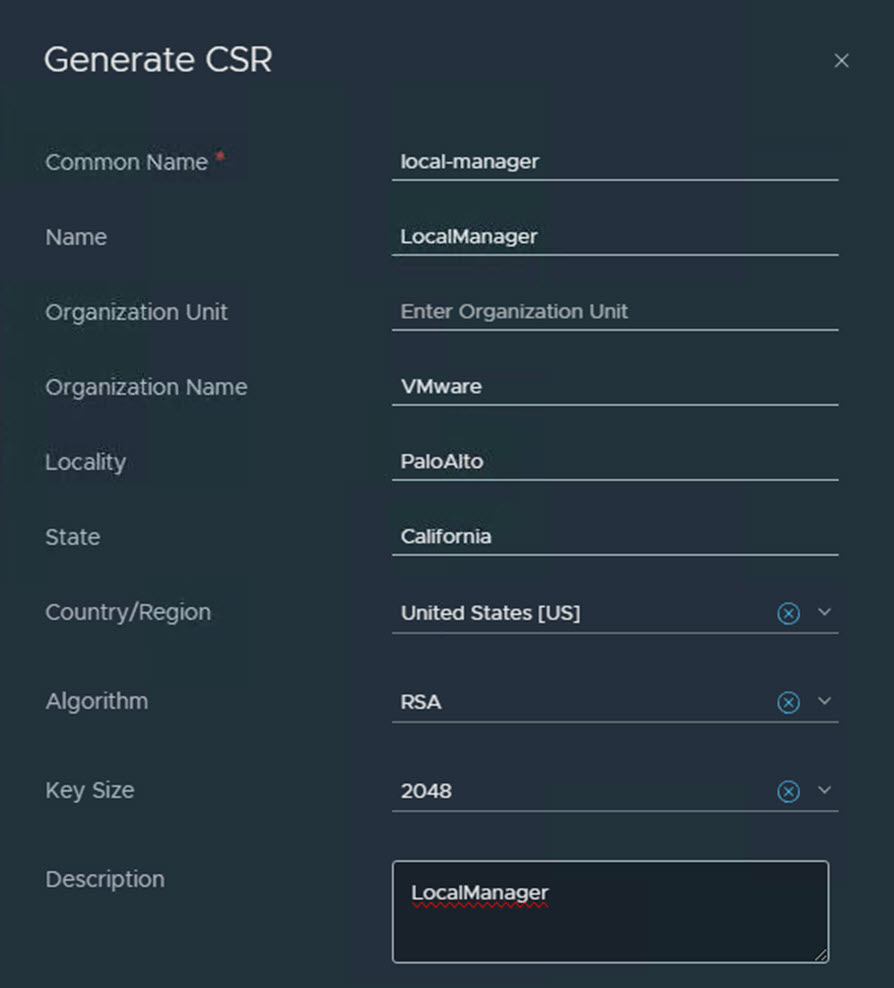
Create self signed certificate through the UI
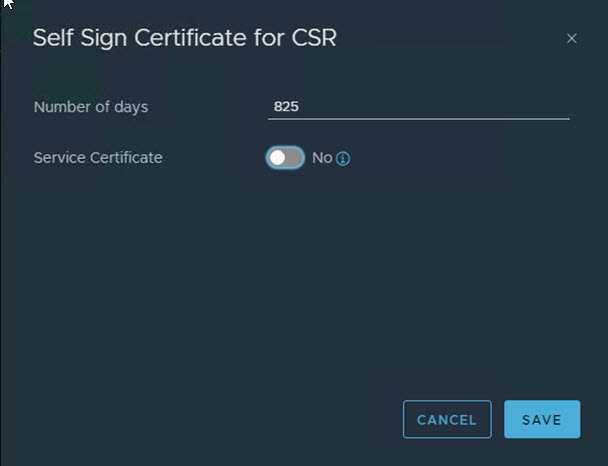
Once the CSR is created, you can be easily create a Self-Signed Certificate using the CSR. Select the sub menu for the CSR and click “Self Sign Certificate for CSR”

Make sure to deselect the Service Certificate. Click Save. The certificate is created.
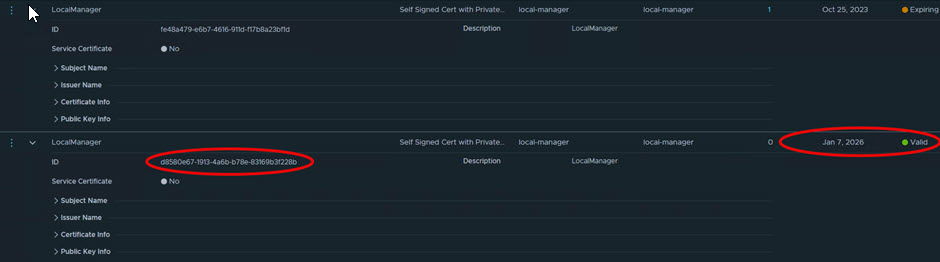
Go to System > Settings > Certificates > Select the newly created certificate
Copy the new certificate ID. You will need this later to activate the certificate for its use.
Activate the certificate using the NSX-T API
Activating the certificate is only possible through the NSX-T API (that’s right, this is you chance to become an NSX-T API Senior Specialist)
Using Postman, you can easily launch API calls. You can download Postman here.
The following VMware documentation is used as a guideline: https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/administration/GUID-50C36862-A29D-48FA-8CE7-697E64E10E37.html
The basic API call for this is : GET https://<nsx-mgr>/api/v1/trust-management/certificates/<cert-id>?action=validate
For the cert-id please use the new certificate ID you just copied
Note that it is a good measure to authorize using your account, e.g. Authorization: Basic Authentication / Password
If Response status is (200) OK, you can be sure the certificate is correct
To activate the LocalManager certificate, you can run the following API call
LocalManager:
POST https://<nsx-mgr>/api/v1/trust-management/certificates/<cert-id>?action=apply_certificate&service_type=<service-type>
POST https://<nsx-mgr>/api/v1/trust-management/certificates/<cert-id>?action=apply_certificate&service_type=LOCAL_MANAGER
For other services, you can run:
![]()
Note that several service-types are available. The following Service_Types are possible : MGMT_CLUSTER, MGMT_PLANE, API, NOTIFICATION_COLLECTOR, SYSLOG_SERVER, RSYSLOG_CLIENT, APH, GLOBAL_MANAGER, LOCAL_MANAGER, CLIENT_AUTH, RMQ, K8S_MSG_CLIENT, WEB_PROXY
The mp-cluster and Tomcat certificates
In an identical way, the mp-cluster and Tomcat certificates can be replaced/renewed.
Note that the service_Type keys for LocalManager, mp-cluster and tomcat translates into LocalManager, MGMT_Cluster and API
- Mp-cluster certificates:
- POST /api/v1/trust-management/certificates/<cert-id>?action=apply_certificate&service_type=MGMT_CLUSTER
- Tomcat certificates
- POST /api/v1/trust-management/certificates/<cert-id>?action=apply_certificate&service_type=API&node_id=<node-id>
- To find node-id : get cluster status
Renewing NSX-T Manager Certificates
Also, the NSX-T certificates need to be visisble in SDDC Manager > Management Domain > Certificates. If this is not the case, you can easily regenerate new NSX-T Manager certificates for the nodes, as well as for the vip, virtual IP.
VMware created the following easy to follow article, KB89921.
From vCenter Server, login with root through SSH
Example code for this:
- python nsxtVmcaCert.py -f nsxt01-1.domain.local -m
- python nsxtVmcaCert.py -f nsxt01-2.domain.local -m
- python nsxtVmcaCert.py -f nsxt01-3.domain.local -m
- python nsxtVmcaCert.py -f nsxt01.domain.local -v
The following articles have guided me:
A next step is to start using VMCA Signed certificates, instead of self-signed certificates : Using VMCA-signed certificates in NSX-T
NSX-T Data Center Administration Guide > Replace Certificates

